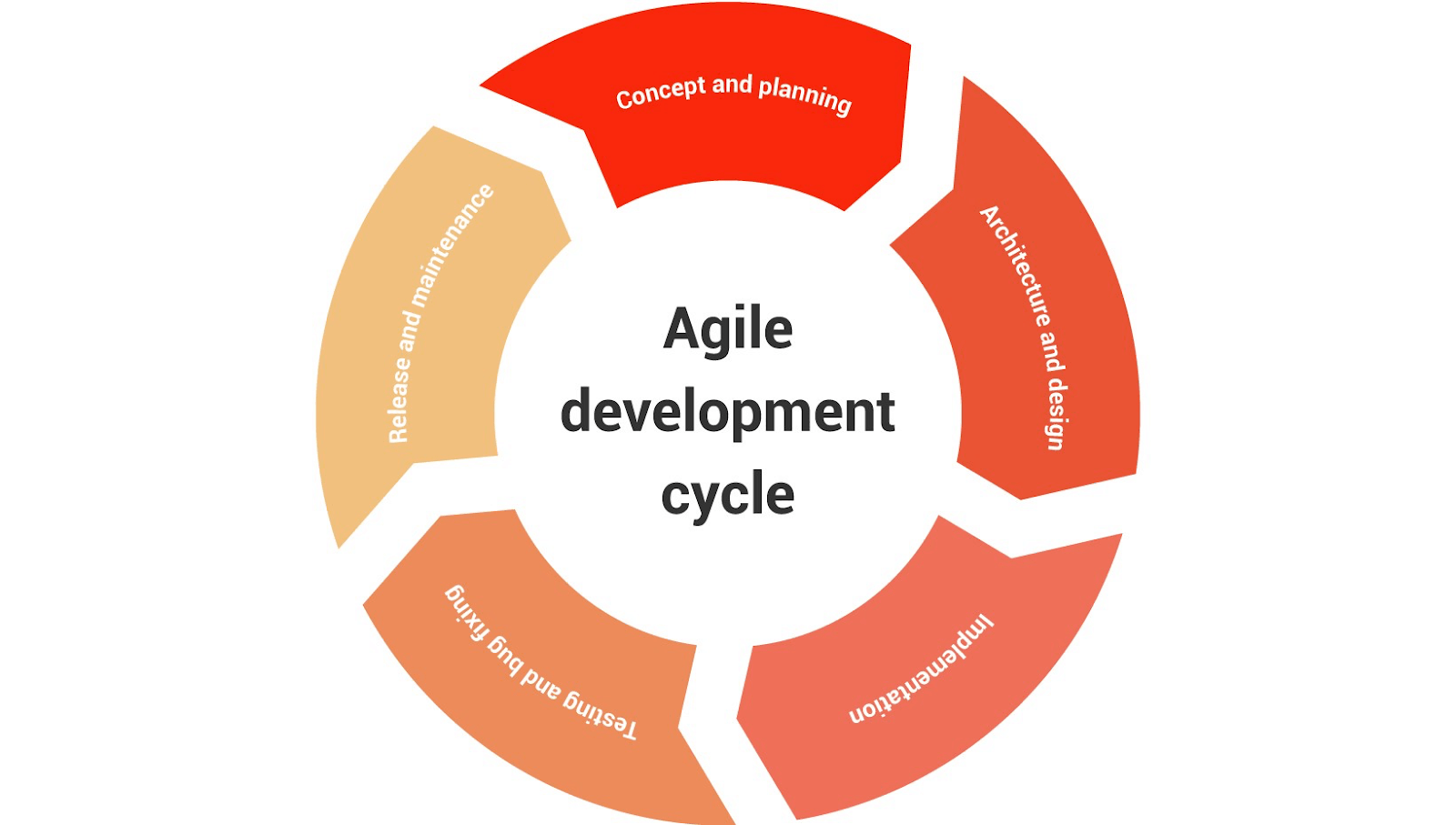
The software development life cycle is a set of steps that help developers plan and create software in an organized way. It has six mains steps:
Each step comes with it’s own security issues that need to be addressed. Failure to address these issues can result in an application full of bugs that, once exploited, can result in downtime, lost revenue, as well as stolen customer information.
This is an extremely common problem, with 90% of the top 100 mobile applications reporting being hacked at least once. Your best chance to prevent these issues is during the development of the application, and that’s precisely where the tips I share in this post can help you.
This guide goes through each individual step of the life cycle and highlights the security practices/actions that should be completed to ensure a secure application. This includes things like industry tools, techniques, and resources you can use to ensure that your application will be secure by the end of the process.
Concept and Planning
This phase is all about defining the application concept and requirements. In other words, it’s important to make sure you have a solid outline of what needs to be done, and that you have a high-level understanding of how you are going to accomplish that.
Outline security and compliance requirements: Outline the technical and regulatory requirements for your application. For technical requirements, this would include making sure you have proper encryption for data in storage and data in transit.
The term “regulatory requirements” refers to understanding the type of data that the software will store and transport—for example, financial information, payment card information, health care, and personally identifiable information.
Each type of data comes with certain regulations on how it needs to be handled, collected, stored, and transported. Therefore, you need to be aware of what information you are collecting and how that information needs to be handled.
Security awareness training: If you are working on a team of developers, you should have time set out to go over security requirements.
If you’re a manager or team lead, you are responsible for organizing this. If you’re just a developer, this is something you should be requesting from your team lead. This ensures both you and everyone on the team understands the requirements set out for the application.
Review third-party software components: Third party components are often used to increase the speed of developing software and add useful functionality. However, they can introduce vulnerabilities in your software, which need to be evaluated before these components are used in your application.
You can begin this evaluation by doing some research into the libraries you are using, which will allow you to see what issues have been reported. For more formal verification, there are companies like veracode that have online guides as well as software solutions for evaluating third-party software for security issues.
Architecture and Design
Threat modeling: This is understanding the probable attack scenarios for your application and coming up with controls that will prevent them from being successful. A common example of this would be an SQL injection, which is where an SQL query is submitted into an input form to extract data from the database.
Ensuring secure design: You want to check that the design of your application adheres to common best practices in software development, such as adding protection for sensitive information and ensuring compliance. Here you can find a list of 10 best practices for software development.
Implementation
Implementation is the process of creating the application, debugging, and creating the first versions of the application that will be tested. The goal in this stage is to create a stable application.
Use secure coding guidelines: These guidelines will warn you of common mistakes that programmers make, allowing you to avoid them and save yourself a lot of time down the road. Some common mistakes include things like storing unencrypted passwords. Here you can find a comprehensive list of the top 10 secure coding practices, as offered by CERT.
Static scanning: Static application scanning tools (SAST) can scan newly written code for vulnerabilities without having to run the application. You can use these as you write your code to check for bugs and correct them before the first version. Here are six SAST tools that you can consider using for your software.
Manual code reviews: After completing the first version of your application, it should have a manual code review done by a senior developer who is knowledgeable on security bugs in software development. Automated tools are much faster, but they can still miss some important issues, so it’s still very beneficial to perform manual reviews.
Testing and Bug Fixing
The purpose of this phase is to discover and fix bugs in the working application. This stage involves running the application and using different types of inputs to see how the application responds.
Fuzzing and dynamic scanning: Dynamic application scanner tools (DAST) test for vulnerabilities by simulating attacks during runtime. Fuzzing involves using automated tools to generate random inputs based on certain patterns to check if the application can handle them correctly. Here you can find a list of some popular DAST tools.
Penetration testing: Penetration tests involve hiring professional security researchers to try and hack into your application in order to find any vulnerabilities that made it this far into your application. You can hire individual companies/teams, or you can use a bug bounty program to crowdsource this step.
Test environment decommissioning: Once a test environment is no longer needed, it should be taken offline or deleted, if it’s a virtual machine. Generally, this is overseen by the DevOps or IT team.
It's common for test environments to have access to the internet to allow developers to connect and do their work. However, sometimes the system remains online even after the project is completed.
Since that environment is not used by anyone, it will remain unpatched. Being internet-facing, it will understandably represent one big easy target for hackers.
Release and Maintenance
This is the phase when the application goes live to its target users. Even though the application is live, this doesn’t mean the work is done. The app needs to be maintained and improved over the course of its life cycle, and possible bugs need to be fixed.
Ongoing security checks and patches: Security checks should be performed on a regular basis by the company’s security team or an independent vendor. Following that, fixes need to be created and released whenever a security issue is found.
These checks don't need to go on indefinitely, but they should go on for at least a few years after the app is released. Furthermore, a statement should be given out to users well in advance of when you plan to stop supporting the application.
End of Life
End of life refers to software that is no longer supported by its developers. This means there will be no more patches, updates, or bug fixes offered. Applications that contain sensitive data also need to have that removed to prevent a data breach due to an old and non-secure application. Any application that isn’t being updated for security-related bugs shouldn’t be considered secure.
Data retention: Government and regulatory bodies define retention requirements for different types of data. It’s important that you confirm your retention requirements and be sure to store the data appropriately before getting rid of an application.
Data disposal: At the end of an application's life, all sensitive information should be securely deleted—including all personal information, encryption keys, or API access keys. The purpose here is to make sure all information is kept confidential and data breaches are prevented. Here are some tips on properly disposing of data.
Fixing Security Issues at Each Stage for the Best Product

With over 90% of top applications in the app store being hacked at least once, this shows that the current process for developing applications isn’t very secure. In this guide I’ve offered you security tips for activities related to each step of the development cycle. Following these tips, you can make sure your applications are much less likely to have security issues.
First in the planning phase, the goal is to properly plan out your application based on the technical and regulatory requirements. Next, you want to design your application based on secure best practices. You also need to implement proper manual and automated testing, and have your application reviewed by subject matter experts. If you lack the internal expertise or funding to hire security professionals for testing, you can use the cost-effective method of bug bounty programs.
Once the application is released, it needs to be checked and patched regularly as new bugs are found. And when its life has ended, the information you need to keep must be secured, and all the remaining information needs to be disposed of to prevent a data leak.