Hollywood has managed to continually misrepresent hackers ever since their introduction in the 80s. They have been portrayed as anti social geniuses who just sit in front of a computer and type fast.
Luckily, the television show Mr. Robot is here to correct that issue. The show comes extremely close to representing a somewhat believable hacker’s universe.
Although it is suitable for most audiences, only programmers will be able to follow up on all the details within the show. Some of them include short lines of code that briefly appear on a monitor, or pieces of software used by some of the characters. Since the creator, Sam Esmail, took advice from skillful programmers, most of what you can see in there is accurate.
This brings us to the revival of cyberpunk.
Think about it.
Gadgets that were once considered “cyberpunk” are now consumer devices. Some examples include robotic limbs, virtual reality headsets, microchip implants, and neural interfaces. The prolific conception of the future in the 80s cyberpunk novels, movies, and comics has started to correlate greatly with our own reality. A great representative of the genre is Ridley Scott’s famous Blade Runner.
At first, being a cyberpunk meant being a lowlife who uses high-tech gadgets to survive in a futuristic dystopia. Today, being a cyberpunk means being offline, off the grid, and in control of data flow. That is what Mr. Robot is partially about.
Hollywood has finally comprehensively explored and portrayed the life of a cyberpunk hacker in a modern society. He is a threat to both criminals and to (apparently) legal corporations as well.
So, what are some of the interesting elements of Mr. Robot, and how do they add to the series’ authenticity?
A Real Hacker
Elliot is the series’ main character. He is a white-hat hacker by day and a black-hat vigilante by night.

The creators already achieve some credibility by making Elliot an employee of a cybersecurity company called Allsafe. We can safely say that one would have to be an extremely skillful engineer in order to work for such a company. It would be like working for a cyber security giant that is employed by Apple, Enron, and General Motors combined. E Corp represents the biggest company in America. That notion itself makes the main character even more believable. Eliot has developed a variety of hacking skills that make him as powerful as he is. Let us go through some of them and see whether they can be applied in the real world.
The Tor Story
Elliot is a kind of hacker that uses his powers for good.
For example, after intercepting the Wi-Fi network of a local cafe, he finds out that the owner is actually running a large-scale child pornography website. Avast security expert Pedram Amini explained that getting hacked through an open Wi-Fi hotspot is highly probable. Anyone can do it just by downloading a piece of free software from the internet, and in case you do not use a safe VPN, you just might get hacked.
Of course, the aforementioned criminal was not that reckless. Elliot had to intercept traffic from one of the previously set up Tor’s exit nodes. This is how he found out the criminal’s location and paid him a little “friendly” visit. For those of you that do not know, the Tor network is used to disguise one’s online identity. It does so by relocating and encrypting one's web traffic across different servers to prevent tracing.
What the Tor story lacks, though, is the differentiation between its top hidden services and the “public internet”. Tor’s hidden services offer an end-to-end encryption method. If one was to control a large portion of the network, they might find IPs of users and the hidden services via their correlation.
Tor is designed in such a way that it does not stop attacks from those who can measure both the incoming and the outgoing traffic of the network. If you can see both flows, it is easy enough to measure them by using a simple statistical approach.
As we can read in the Tor design paper, the program itself is not intended to fight end-to-end intersection or timing attacks. This is why in 2014 there was a group of relays that was assumed to have been trying to deanonymize users. Users who utilized Tor’s hidden services were the main targets.
Krista Was a Sitting Duck
Let’s get back to Elliot. He is a sociopath. He explores the world by hacking the people he meets. It is his way of getting to know them and participating in social interaction. By exercising his hacking power, he plays his role within society.
“I don't just hack you, Krista. I hack everyone.”
Krista, Elliot’s therapist, was an easy target. He says that hacking her was simple. Her password was the name of her favorite artist, combined with her birth date written out backwards. How obvious is that?
The problem with this is that a large number of people all over the world think of passwords that are just too simple. They are not aware of the amount of information they leave behind while maniacally surfing the web or downloading a certain coupon. Social media accounts are also full of valuable personal information. It can be fed into a simple password cracking tool which will be enough to crack it most of the time.
Et tu, Brute?
Krista’s boyfriend Michael was not spared either. He was subject to an effective brute-force attack. Of course, the cryptanalytic attack that was aimed at retrieving encrypted data was used because there were no other frailties in the encryption system.
For those that do not know, a brute-force attack is similar in its nature to a dictionary attack, whereas the latter uses a more specific targeting system. To exemplify, a brute-force attack was responsible for the infamous Celebgate scandal.
You have to watch out for your non-famous behind as well these days. One of the ways is to use some kind of an offline storage device.
Elliot uses CDs to avoid having his data stored in the cloud. This might seem ridiculous today, especially because you can find many cloud storage apps with solid encryption systems. I would recommend Mega, 4Shared, or pCloud (which even set up a hacker challenge to prove its impenetrability). After reading some of the 4Shared reviews, though, I decided to try it out over the others and still remain unhacked.
Of course, any kind of digital storage can be an easy target for an experienced hacker. You have to be careful about your digital footprint and the files you download. Since this is the reason that Elliot is using CDs, and could be a whole new article topic, let us get back to our Mr. Robot analysis.
The E Corp Hack
Large companies are also vulnerable to attacks from the more experienced hackers. Even Allsafe’s client, the multinational conglomerate E Corp, suffered a catastrophic security breach. Ironically, the company suffered a DDoS attack. The attack was based on rootkits that contaminated a large number of servers.
What Is a DDoS Attack?
The goal of a Distributed Denial of Service (DDoS) attack is to disable a server by overflooding it with service requests. These kinds of attacks are sent by botnets in order to overload the server. The server itself cannot withstand so many requests and thus becomes rendered unresponsive and ultimately useless. These kinds of attacks are so effective because one can easily guess the pattern of information that a company gives out through its employees. For example, if one email looks like “name.surname@ecorp.com”, a hacker can easily guess the remaining hundreds of emails, just by looking at the list of all the company’s employees. Once he has collected all the information, the attacker can run it through a password cracking software and take over control of the routers.
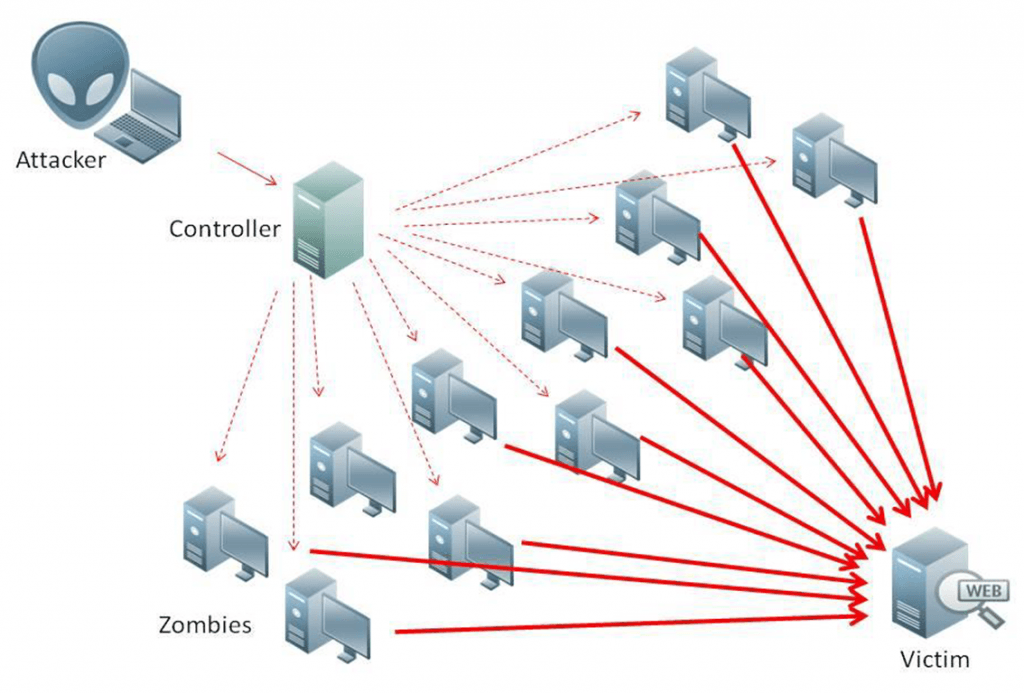
DDoS attacks are mostly targeted at larger businesses; however, hackers tend to use individual routers to facilitate their attacks as well. You might be helping a criminal without even realizing it! In fact, millions of consumer routers are found to be vulnerable to such cybersecurity threats even as we “speak”.
The Actual Coding
The hacking in the series is portrayed as accurately as possible. Programmers are analyzing Elliot’s actions by looking at screenshots of various commands which randomly appear throughout the show. There is a lot of disagreement over whether these lines of code are entirely accurate or not. It seems that there are a few loopholes, but those just allow for the many interesting new ideas spread all over the internet. What comes next is a list of some of the commands used in Mr. Robot.
- root@elliot—Elliot chooses root over sudo, but does it make any sense? Since he is trying to find a machine on the network, it is possible that he has to use root because of the various necessary ping switches.
- astsu – info -backup -short—This command is actually unique to the series, and it most likely stands for A Server StatuS Utility. The commands are self evident: info (server information); backup (prints out the backup server); short (the details will be brief). The output is nothing special, either (he should have probably gone with -b or –backup). It is a bit strange that he did not spend as much time on the output as he did on parsing the input parameters.
- astsu – ifconfig – disable—Elliot loves his spaces. He is obviously disabling the ethernet interfaces.
- astsu -open port: * -persistent—The astsu command is powerful indeed! Elliot uses it to shut down all the ports on the servers. I wonder if the command uses iptables?
- astu -rm -norecycle /root/ fsociety/—Elliot almost deleted his entire root directory. Here, we see him skipping the recycle bin, but cancelling the command just in time.
While there are minor inconsistencies, those can be forgiven since the creators paid such great attention to detail when it comes to the actual hacking. Now let us go through some of Elliot’s hacking tools.
Hacking Tools in Mr. Robot
The series’ creators found a reasonable balance between basic Hollywood entertainment and technical accuracy required for the portrayal of a hacker. Let us see just how technical they got. Here are some of the hacking tools that we can see in the series:
Canbus Hacking
In one of the screenshots we can see candump. It is a Linux utility used for viewing canbus messages. Canbus hacking is very popular right now as it is being used for white-hat car hacking. Security specialists use it, too, for testing out the vulnerabilities of a car computer.
Kali Linux
There are multiple references to Kali Linux throughout the show. It is an OS dedicated to penetration testing. It comes with preconfigured hacking tools and is great for beginners because it is easy to configure. Nevertheless, you would have to be acquainted with the Linux terminal and do some reading and research as well. Of course, the program should be used only for the purposes of learning, unless you work as a cybersecurity expert and need to do a lot of pen testing.
Bluetooth Scanner
This tool is a part of Linux distribution and is used for getting as much data as possible from a Bluetooth connected device without having to pair. As we can see from the window’s title bar, Kali Linux is clearly their OS of choice.
Metasploit Framenetwork
Meterpreter is an essential penetration testing tool by Rapid7. Its shell enables attackers to take full control of one’s system and freely move around the network. It is a powerful tool which appears just briefly enough to get noticed.
Netscape Navigator
Elliot mentions that he used Netscape Navigator and Windows 95 while he took his first hacking steps. This browser is extremely useful for the main character because of its simplicity. Furthermore, it is the first browser that Elliot ever used. It was invented by a hacker named Marc Andreessen in 1993. Netscape Navigator is especially useful for social engineering and web application attacks, but you will have to do a lot of reading in order to truly grasp its capabilities. We can see a screenshot of the browser as Elliot analyzes a source.
Bluesniff
This is another tool used for attacking devices equipped with Bluetooth. Here, we can see a man-in-the-middle attack though a victim’s Bluetooth keyboard. A Meterpreter shell is then dropped onto the system in order to access the network.
Social Engineer Toolkit
Social Engineer Toolkit (SET) is used for making social engineering attacks easier. Phishing attacks, wireless access points, and decoy websites can all be set up through the SET’s system. Here is an example of an SMS module used in the series.
A Simple USB Drive
Elliot’s accomplice dropped a heapful of flash drives in the police parking lot. What happened next was awesome. A security guard picked up one of the drives and injected it into his computer. It was a sneaky, but effective, trick to pass on the code unnoticed where network access is limited.
Most of these tools are open source and easily acquirable. There are tons of tutorials and documentation all over the web. It is the incorporation of these very tools that makes hacking in Mr. Robot even more authentic.
A Cyberpunk Universe
The 80s were a time when cyberpunk flourished as a genre. The genre itself deals with a dystopian future, in which an individual is oppressed and forced to move out of the confines of an automated and brainless consumer society.
Today, cyberpunk is back. But this time, it’s not as a piece of science fiction, but our reality, as suggested by Sam Esmail. In this Reddit AMA, he explains that he wanted to bring cyberpunk back.
How Did They Do It?
They incorporated many cyberpunk elements within the story. Some would say that the setup is similar to Neuromancer. Elliot is the antisocial, introverted hacker antagonist with schizophrenia and a drug addiction problem. He is set to take down the gigantic Evil Corp and save billions of lives with his programming skills. Another classic character in the show is the Asian hacker Whiterose, a transgender person operating out of a Faraday cage! Elliot’s sister Darlene is also a true renegade. She looks like trouble and is a true addition to the fsociety team. She is fierce, bold, knowledgeable, and ruthless. In addition to that, she looks like a cyber-hippy-punk, with dark makeup and a piercing.
Sam Esmail used a basic 80s cyberpunk story premise, but the reason why the show became so popular is due to its connection to our current reality. The show’s creator wants to uncover the weirdness of our world. We are now participants of the dystopian future that we once conceived and feared.
Elliot is a contemporary cyberpunk. What was once off-grid is now offline. The more you hide your trace, the better chances you have of keeping your information private and prevent it from becoming big data. Big data is of great value in today’s world. Companies gather it for analyzing consumers’ needs, and Elliot uses it for destroying those very same enterprises.
The Anti-Social Aspect
Can we escape the system? Can we hack the Matrix? The battle of fsociety and E Corp is similar to the one of David and Goliath. But does David actually win in the real world?
The notion of having no escape from a world he despises makes Elliot subject to depression, even madness. He gives in to morphine addiction and suffers all throughout the show. The antisocial aspects of the main character and his gang are extremely important when it comes to conveying the message of why they are so frustrated with reality.
All of the characters are on the verge of falling apart. Darlene is almost too dedicated to destroying the E Corp, but that kind of desperation is required in order to make the character believable. Her life depends on it, on that very storyline. She is also a skilled hacker and a teamplayer and tries to justify fsociety’s actions at all costs.
Darlene is also responsible for the greatest twist of the series, too, but I will not give away too much.
As Authentic as It Gets
Mr. Robot is unmistakably the best show out there when it comes to an accurate portrayal of hackers in our time. Some argue that it could be the best show of 2015. It presents characters in an authentic, seamless manner. One part of the series’ success was that connection with the characters, which we as audience members can feel throughout the season.
Furthermore, hackers in Mr. Robot use real tools and pieces of software, unlike what can be seen in most of Hollywood productions. This is why the series is so appealing to software engineers—we can enjoy it, too, since some of the best engineers were involved in the creation of the show.
Cyberpunk is here once more, and we can thank Sam Esmail for doing an excellent job of pointing that out.
Just like hacking, marketing tends to get a bad rep. Don't worry — it isn't a dirty word. If you're slaving away at a job that under-values you, check out my course “How to Market Yourself as a Software Developer”.


